In September 2023, Armour Insurance and Accurate Network Services teamed up to host the first-ever Think Like a Hacker event. The event was all about how to protect yourself, your clients, and your business from cyber security threats. We wanted to take this opportunity to share some of the insights and maybe allow you to Think Like a Hacker too.
Presentation by Constable Jon Cook - RCMP Cybercrimes Division
We were fortunate enough to have Jon Cook from the RCMP as the keynote speaker for the event. Constable Cook shared some excellent information on how to "Think Like a Hacker". The overall message boiled down to taking a cautious, well-informed, approach to cyber security.
Here are a few short clips from the presentation.
How are Small and Medium Businesses at Risk of Cyber Attacks?
To understand how to protect your business from cyber threats, it's important to understand what can make you a target. A common adage in the world of cyber security is that small and medium sized businesses are less at risk of cyber attacks than larger organizations. We learned that the opposite is often true.
Many cyber criminals see small and medium-sized businesses as low hanging fruit. Generally speaking, businesses under 100 people will invest less money into cyber security than larger businesses will. In fact, Constable Cook informed us that the majority of cybercrime cases that the RCMP handles are for small and medium businesses. While cybercriminals know that smaller businesses will have lower returns, they also see them as being quick and easy targets.
What Can Make Your Business Vulnerable to a Cyber Attack?
There are several factors that can make your business vulnerable to cyber attacks. Here is a list of just a few factors that can leave you exposed:
- Outdated software or operating systems
- Weak passwords and/or authentication mechanisms
- Lack of cybersecurity awareness
- Business size and relevance
Outdated Software or Operating Systems
Using outdated software in your organization can put your business in the crosshairs. Oftentimes, software companies stop updating older versions of their software after a certain point. This can mean that bugs and weak spots aren't rectified going forward. This can be a metaphorical ticking time bomb as any hacker with knowledge of the bug can break through with ease.
Maintaining an up to date software and hardware gives you a good first line of defense to keep your information secure. Turning on automatic updates can ensure you get the most up to date software patches available.
Weak Passwords and/or Authentication Mechanisms
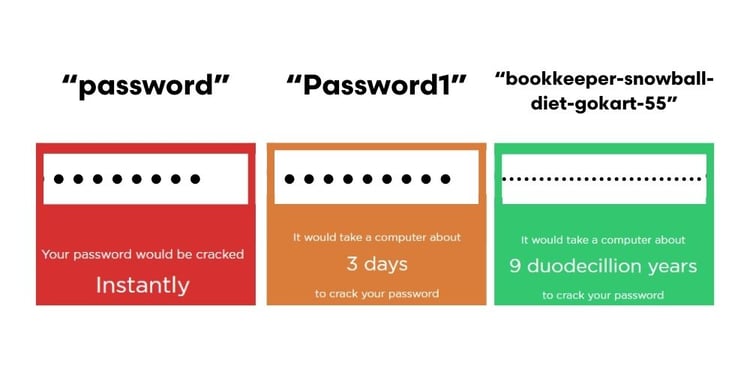
You're probably aware that the days of having your password as "password" are long behind us. But the days of having a password are also quickly coming to an end. For many, the change from "password" to "Password1!" was good enough. Unfortunately, this is simply not the case. One of the new password best practices is to have a passphrase made of completely random words.
An example could look something like any of the following:
- bookkeeper-snowball-diet-gokart-55
- bling-hamburger-store-martian-97
- sports-cake-business-shield-83
Modern technology has made it easier than ever before to crack a password. By implementing unique passphrases into your cybersecurity, you can take your password from easily cracked, to nearly impossible to crack.
Another tool at your disposal is implementing two-factor authentication on your accounts. Having two-factor authentication can prevent saved passwords from rendering your defenses useless. At Armour Insurance, we use the Authenticator app which requires a numeric code and biometric security to access.

Lack of Cyber Security Awareness
Having poor cyber security knowledge and training in an organization can leave you vulnerable to preventable attacks. Attacks like phishing and smishing are designed to go after unsuspecting victims and can be easily prevented with a well-trained staff. Having cyber training at all levels of your organization can help prevent cyber attacks.
Business Size and Relevance
While it was mentioned previously that small and medium businesses are often the target of cyber attacks, other factors may increase risk. Businesses with access to sensitive/valuable data and businesses with perceived low cyber security are common targets.
Organizations with sensitive or valuable data may include any number of industries. Here are a few examples:
- Medical organizations (medical records, patient data, etc.)
- Financial institutions (financial statements, client funds, etc.)
- Insurance companies (client records, financial information, etc.)
- Others
When your organization has data like this, it can put you in the crosshairs for a cyber attack. Organizations with perceived low cyber security and high-value data are in the greatest risk category of an attack.
How Can I Improve My Organizations Cyber Security?
Making an improvement in your organizations cyber security could be easier than you think. Here are a few steps you can take to help:
- Get a quote on cyber insurance
- Develop a cyber incident response plan and practice that plan
- Assign a privacy officer
- Know your infrastructure and the data you have
Get a Quote on Cyber Insurance
If you're skeptical about an insurance company telling you to get a quote on one of their products, that would be fair skepticism. That being said, even if you're not in the market for a cyber insurance policy, getting a quote can be a good first step in determining your cyber risk.
Develop a Cyber Incident Response Plan
Organizations of any size should have a cyber incident response plan. Response plans should consist of key components.
Prepare
Set clear objectives for your incident response strategy and develop a comprehensive plan to strengthen your organization's security, visibility, and recovery capabilities. Establish a robust backup system to support data restoration during downtime or disruptions. Regularly update and patch your software and hardware to minimize vulnerabilities. Test your incident response plan, analyze the results, and refine your plan accordingly.
Observe
Continuously monitor your networks, systems, and connected devices to proactively identify any potential threats. Make it a regular practice to generate comprehensive reports and carefully document all events and potential incidents that occur. With a thorough analysis of these occurrences, determine when it is necessary to activate your incident response plan. Consider determining the most suitable frequency and intensity for your monitoring efforts, whether it involves maintaining a constant 24/7 view, or adopting a more flexible as-needed approach.
Resolve
To effectively address and mitigate the threat, it is crucial to have a thorough understanding of the situation. Take immediate action by disconnecting systems and devices to prevent further harm. Implement measures to isolate systems, suspend employee access, and detect/prevent any additional intrusions. Restore systems from backup to completely eliminate the intrusion. Ensure all devices are protected by running anti-malware/anti-virus software and promptly patching/updating if vulnerabilities are identified. Preserve evidence/documentation to assist in analysis and establish preventive measures for future incidents.
*This is also the stage where you would be in contact with a cyber insurance company. They can provide guidance and may have their response team handle things from there.
Understand
Determine the root cause of the incident, collaborate closely with the response team, and carefully assess the effectiveness of response processes. Develop a comprehensive document that captures valuable lessons learned and outlines necessary adjustments for future incidents. Thoroughly document the steps taken to uncover and resolve the incident, creating a valuable resource for expediting recovery and improving overall effectiveness.
Do you want a free copy of our Cyber Incident Response Guide?
Assign a Privacy Officer
Depending on your industry, you may already have legal or regulatory requirements to have a privacy officer. Regardless of whether or not you're obligated to have a privacy officer, it is a good idea to have a designated person as a privacy officer.
Privacy officers are typically responsible for establishing privacy policies and procedures, monitoring compliance controls, overseeing privacy impact assessments, and ensuring staff are properly trained for cyber and privacy protocols. By simply having a privacy officer, your organization is a much less appealing target to a cybercriminal.
Know Your Cyber Infrastructure and Data You Have
As Constable Jon Cook had stated in the earlier video, having a good understanding of your cyber security infrastructure can be a great help in the event of a cyber event. It can:
- Aid law enforcement when responding to a cybercrime in process
- Help IT or cybersecurity isolate the issue
- Determine the areas impacted by the breach
Having ID numbers on all devices and even a diagram of your IT infrastructure can be incredibly helpful when responding to a cyber event. An additional piece of helpful information is having a strong knowledge and understanding of the data that you're storing. If you have sensitive client data that you're storing, ensure that is is both relevant and well protected. If you have unnecessary customer data on your servers, it is an unnecessary risk and liability to you, your clients, and your business.
Armour Think Like a Hacker Event
Most of the information in this article was a part of the Armour and Accurate Think Like a Hacker event of 2023. We were fortunate enough to have a panel of experts for a moderated Q & A session, a keynote presentation by Constable Jon Cook, and nearly 100 guests in attendance for the event.
We owe a thank you to our panel of experts for sharing their insights with our guests.
- Constable Jon Cook – Cybercrime Investigator with the RCMP
- Jean Eaton – Practical Privacy Coach with Information Managers
- Mark Linton – Cyber Security Expert at Triple Check Consulting
- Rob Marusin – Insurance Expert and President of Armour Insurance
- Booker Zaytsoff – IT Expert and Director at Accurate Network Services
Upon the completion of the keynote presentation and the Q and A session, we asked a few of our guests at the event what their takeaway was from the Think Like a Hacker event. Here is what they had to say:
So, What Happens When you Think Like a Hacker?
In your business or organization, it's important to think about where you're vulnerable. When you think like a hacker, you can find the areas of your business that could be a weak spot or an easy target. By thinking like a hacker, you're promoting a culture of cyber security. A culture of cyber security can make your business less vulnerable to a cyber attack and it can make it easier to identify a cyber event when it happens.
If you're feeling inspired to get a cyber risk assessment and a quote on cyber insurance, click the link below: